What is SSRF?
Server-Side Request Forgery (SSRF) is a web security vulnerability that allows an attacker to manipulate a web application to send unauthorized requests from the server itself. This vulnerability is dangerous because it can be used to access internal systems, retrieve sensitive data, or interact with services that are not meant to be exposed to the public.
Unlike client-side vulnerabilities such as Cross-Site Scripting (XSS), SSRF exploits a flaw in how the server processes requests. It tricks the server into making unintended requests, which can be leveraged to perform actions like:
- Bypassing firewall restrictions
- Scanning internal networks
- Accessing internal APIs and cloud metadata services
- Extracting sensitive information
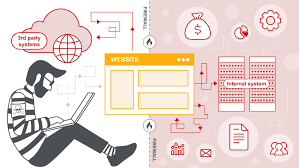
How Does SSRF Work?
SSRF occurs when an application allows users to specify a URL or an endpoint that the server will fetch. If the server does not properly validate and restrict these requests, an attacker can exploit this functionality to make the server fetch data from unauthorized sources.
Basic Example of SSRF
Imagine a web application that fetches external images using a URL provided by the user.
@app.route('/fetch')
def fetch():
image_url = request.args.get('url')
response = requests.get(image_url)
return Response(response.content, mimetype="image/jpeg")
If the application does not validate the URL, an attacker could supply an internal endpoint:
<http://example.com/fetch?url=http://127.0.0.1/admin>
If an internal admin panel is hosted on http://127.0.0.1/admin, the server will attempt to fetch it and might return its contents to the attacker.
Real-World Example of SSRF
Exploiting Cloud Metadata API
Many cloud service providers (like AWS, Google Cloud, and Azure) have metadata APIs accessible internally through a special IP address (169.254.169.254). This API often contains credentials, configurations, and sensitive information about the server.
If an application is vulnerable to SSRF, an attacker could craft a request like:
<http://example.com/fetch?url=http://169.254.169.254/latest/meta-data/>
If successful, this request can return sensitive AWS instance metadata, including temporary security credentials:
<http://example.com/fetch?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/>
This could allow the attacker to escalate privileges and gain full access to the cloud infrastructure.
Types of SSRF Attacks
- Basic SSRF – The attacker uses the vulnerability to retrieve data from internal systems.
- Blind SSRF – The response is not directly visible to the attacker, but the attack still impacts internal resources.
- SSRF to Remote Code Execution (RCE) – In some cases, SSRF can be chained with other vulnerabilities to execute arbitrary commands on the server.
How to Prevent SSRF?
- Whitelist Allowed Domains – Restrict requests to a predefined set of trusted domains.
- Validate and Sanitize User Input – Block internal IP ranges (
127.0.0.1,169.254.169.254, etc.). - Use Firewalls and Network Segmentation – Prevent internal resources from being accessed externally.
- Disable Unnecessary Services – If metadata services are not needed, disable access to them.
- Use a Proxy for Outbound Requests – Control and monitor requests made by the server.
Conclusion
SSRF is a critical vulnerability, listed among the OWASP Top 10, and it can lead to devastating consequences, including unauthorized access to internal systems and cloud resources. Developers should implement strict validation mechanisms, security teams should test regularly with tools like Burp Suite and OWASP ZAP, and organizations should adopt secure coding practices to prevent exploitation.



